ECU Security Bypass: Understanding Risks and Techniques 🔧🚗
The automotive industry has seen significant advancements in electronic control units (ECUs) over the years. With these advancements, however, come challenges related to security. This article delves into ECU security bypass methods, their implications for tuning professionals, and the tools that can assist in this process.
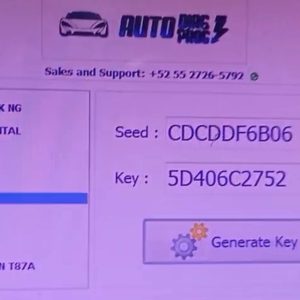
What is ECU Security Bypass? ⚙️
ECU security bypass refers to methods used to circumvent the security mechanisms of an ECU. This is often necessary for:
- Reading and writing to locked ECUs
- Performing remapping and tuning
- Diagnosing issues in a secure environment
Bypassing security can be a double-edged sword, as it may lead to unintended consequences if not done correctly.
Common Techniques for ECU Security Bypass 🔧
Several techniques are commonly employed in the industry:
- Boot Mode Access: This method involves accessing the ECU in a low-level mode, allowing for direct communication. It requires specific knowledge of the ECU architecture.
- OBD Port Access: Some tools allow access to the ECU via the OBD-II port, but this often depends on the vehicle’s security protocols.
- Hardware Modifications: In certain cases, physical modifications to the ECU may be needed to bypass security features. This is risky and should only be performed by experienced professionals.
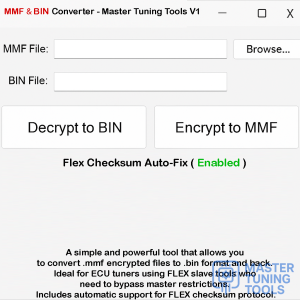
Tools for ECU Security Bypass 🛠️
Utilizing the right tools can significantly streamline the bypass process. Here are a few popular options:
- KESS3: A versatile tool for reading and writing ECU data, particularly useful for OBD access.
- FLEX: Known for its extensive protocol coverage, FLEX is effective for both tuning and security bypass.
- CMDFlash: This tool excels in boot mode programming, making it a solid choice for advanced users.
Risks of ECU Security Bypass ⚠️
While bypassing security can open new avenues for tuning, it is essential to consider the risks:
- ✅ Potential for Damage: Incorrect procedures can lead to ECU bricking.
- ❌ Legal Implications: Bypassing security may violate manufacturer warranties or local laws.
- ✅ Loss of Data: Improper handling can result in losing factory settings.
Best Practices for ECU Security Bypass ✅
To mitigate risks associated with ECU security bypass, consider the following best practices:
- ➡️ Always create a backup of the original ECU data before attempting any modifications.
- ➡️ Use reputable tools and software to ensure compatibility and reliability.
- ➡️ Stay updated with the latest security protocols and ECU architectures.
In conclusion, ECU security bypass is a critical skill for professional tuners and mechanics. Understanding the techniques, tools, and risks involved is essential for successful ECU remapping and tuning. For more information and to explore related tools, visit mastertuningtools.com.